After powering up the virtual machine i ran an nmap default scan to find versions of any applications running

Seeing there is an Apache server running, i visited the site

After a bit of playing around, nothing was interactive. I looked at the hint available on the Agent T room

Opening up the page inspector and reloaded the page

Knowing that there must be something here in the HTTP headers – i analyzed a few of the GET requests
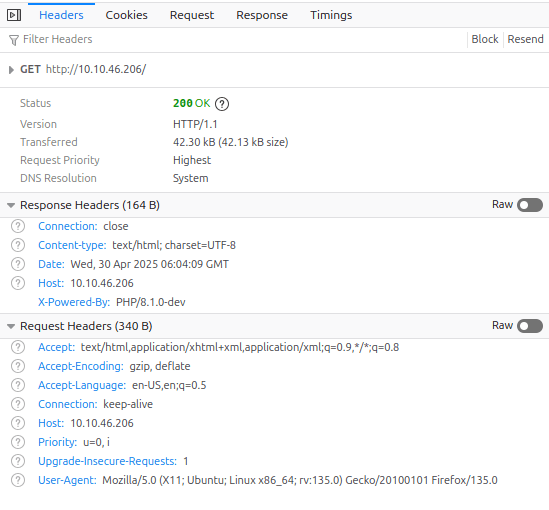
The first GET request shows what is also visible in the nmap scan – The webpage is running PHP 8.1.0
A quick Google search indicates there is a backdoor vulnerability on this version of PHP

Going to Github by user flast101 has a great python script to execute the backdoor

I downloaded the script, using chmod +x to make the script executable and ran it

Instantly having root access to the server
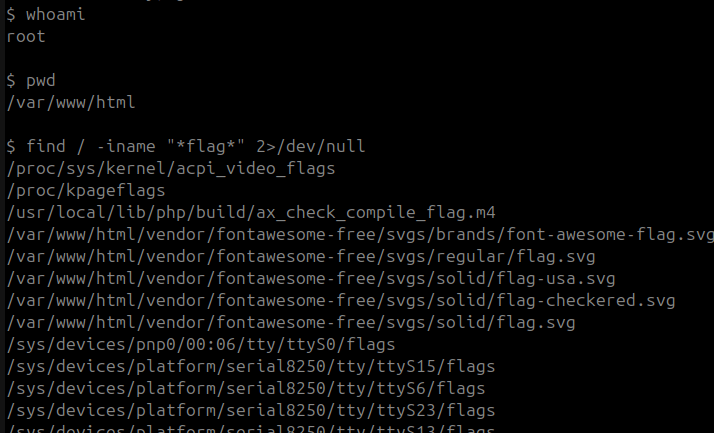
i did a search for anything with the word “flag” in it as the Agent T room is requesting a flag

And found the flag
Writeup by isko3k
Attack box by Created by
